- Creating Logon Scripts - Windows TechNet
- ASA 8.x VPN Access With The AnyConnect SSL VPN Client Configuration Example
- Anyconnect Sbl Download
AnyConnect SBL is to allow users to connect to the VPN before signing into their Laptop/Desktop. This is useful for companies that want all of their Laptops to use Active Directory to sign into the laptop but need a secure way to reach the AD Server.
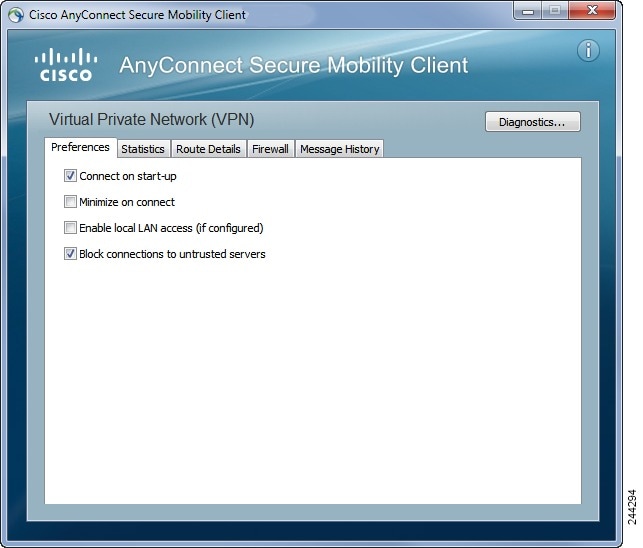
Anyconnect VPN client Start Before Login (SBL) tips Lessons learned tips for enabling Start Before Login for anyconnect vpn client. This is going to be an add-on post to a documented procedure. With the AnyConnect 'Start Before Logon module (GINA)' package, you can establish a VPN connection to our infrastructure before you log in to Windows. This can be installed via 'Software Center' found in the Startmenu on SCS managed Windows machines that are subscribed to Software Support.
- Must be using the AnyConnect client and the user must be using a Windows 7 or XP machine. This does not work with 8+ from what I have tested.
- Create the default configuration for the AnyConnect VPN.
Note: If you plan on using a Self Signed Certificate the FQDN must be the IP of the firewall or the customer must setup a DNS entry for the FQDN. - Upload the SBL.xml page to the firewall.
The key thing to change is the value between the <UseStartBeforeLogon> to true. If you are currently using a xml profile, you can also edit this line, or add, for this configuration to work. - Add the SBL.xml file to the webvpn settings.
ASA 8.x Code
webvpnsvc profiles SBL disk0:/SBL.xmlASA 9.x Code
webvpn
anyconnect profiles SignOn disk0:/SBL.xml - Add this profile along with the vpngina module to that group-policy that you applied to your AnyConnect VPN tunnel-group.ASA 8.x Code
webvpnsvc profiles value SignOnwebvpnanyconnect profiles value SBL - Connect to the VPN as a new session to make sure that your new profile gets pushed from the Firewall.
- If you used an Authorized Certificate – proceed to step 8, otherwise, follow step 9 for Self Signed Certificates
Self Signed Certificate steps
- Go to https://<Firewall IP>
- Click on the Lock icon in the URL. Click more information then click view certificate.
- Go to the details tab and click export. Save it as a X.509 certificate with chain (PEM) (*.crt,*.pem).
- Run Microsoft Management Console, by entering “mmc” in the run or search box (requires administrator permissions).
- In the MMC utility go to file and click on add/remove snap-in.
- You will want to add the certificates snap, and set it to computer then local computer.
- Open trusted root certificates and right click on certificates and click import.
- Locate the file you saved earlier, then import that file.
- Save the configuration. The name doesn’t matter.
- Reboot the machine. Once rebooted you can click on switch users and see the following icon:
- Use this button to login to the VPN before logging into the OS.
 Never mind. It's a selection in the Group Policy section.
Never mind. It's a selection in the Group Policy section.
http://www.cisco.com/c/en/us/td/docs/security/vpn_client/anyconnect/anyconnect40/administration/guid...
From:

Enable Additional AnyConnect Modules
To enable additional features, specify the new module names in the group-policy or Local Users configuration. Be aware that enabling additional modules impacts download time. When you enable features, AnyConnect must download those modules to the VPN endpoints.
Creating Logon Scripts - Windows TechNet
NoteIf you choose Start Before Logon, you must also enable this feature in the AnyConnect client profile.ProcedureStep 1 In ASDM go toConfiguration >Remote Access VPN >Network (Client) Access >Group Policies.Step 2 Select a group policy and clickEdit or Add a new group policy.Step 3 In the navigation pane, selectVPN Policy >AnyConnect Client. AtClient Modules to Download, clickAdd and choose each module you want to add to this group policy. The modules that are available are the ones you added or uploaded to the ASA.Step 4 ClickApply and save your changes to the group policy.ASA 8.x VPN Access With The AnyConnect SSL VPN Client Configuration Example

Anyconnect Sbl Download
